Did you know that during the early stages of CI/CD adoption, security was often an afterthought? Developers focused primarily on accelerating development and deployment cycles, with limited emphasis on security. Security checks were typically manual and performed at irregular intervals, leading to the rapid growth of vulnerabilities in software.
As organizations recognized the importance of security in CI/CD pipelines, there was a shift towards integrating security tools and processes into the development lifecycle. Automated security scanning tools became common, allowing for the detection of vulnerabilities at every stage of the pipeline. This integration helped in identifying and addressing security issues more proactively.
In this blog post, we'll delve into the importance of securing CI/CD pipelines and explore strategies for patching the holes in your CI/CD security to prevent secrets from leaking.
Understanding CI/CD Security
CI/CD (Continuous Integration/Continuous Deployment) security refers to the measures and practices implemented to ensure the security of software development processes that utilize these pipelines. It is a methodology used in software development where code changes are automatically built, tested, and deployed to production environments in a continuous manner. CI/CD pipelines automate these processes, enabling rapid and frequent delivery of software updates.
It is a crucial aspect of modern software development practices, especially considering the rapid pace of software delivery and the increasing sophistication of cyber threats. According to Techstrong Research, while 84% of respondents acknowledged the importance of CI/CD pipeline security, over 20% of organizations have reported a security incident within their pipelines in the previous year. These statistics show that even though organizations are aware of its importance, they still struggle in effective implementation of CI/CD Security
How CI/CD Optimizes Software Delivery
CI/CD holds significant importance in software development, particularly within development companies, for several compelling reasons.
Firstly, it expedites the time to market by facilitating frequent integration of code changes and rapid deployment, enabling companies to swiftly deliver new features and updates to users, thus maintaining a competitive edge.
Secondly, it enhances quality assurance by automatically testing code changes upon integration, detecting and rectifying bugs early in the development process, thereby ensuring higher software quality and reducing the likelihood of critical defects reaching production.
Thirdly, it mitigates risks associated with manual processes by automating build, test, and deployment procedures, resulting in more reliable software releases and minimizing the risk of downtime or service disruptions.
Additionally, CI/CD fosters increased collaboration among developers, testers, and operations teams by providing a unified platform for continuous integration and deployment, thereby enhancing communication and teamwork efficiency. Furthermore, it offers scalability benefits, accommodates multiple teams working on diverse projects simultaneously, and ensures consistent and reliable development processes irrespective of project size or complexity.
Are you ready to bring your idea to life? Reach out to us now and discover how our website application development services can elevate your brand and drive your growth!
How to Secure CI/CD Pipelines for Safe Deployment
Securing a CI/CD pipeline is crucial for ensuring the integrity and safety of software delivery processes. Here are some strategies and best practices for the same:
Testing:
Static Code Analysis:
Integrate tools like SonarQube or Checkmarx into your CI/CD pipeline to analyze code for security vulnerabilities and coding best practices.
Dynamic Application Security Testing (DAST):
Automate security testing by incorporating DAST tools like OWASP ZAP or Burp Suite into your pipeline to detect vulnerabilities in running applications.
Automation Control:
Version Control:
Use version control systems like Git and implement strong access controls to manage changes to the CI/CD pipeline configuration and scripts.
Immutable Infrastructure:
Implement immutable infrastructure patterns where the infrastructure is treated as disposable and can be rebuilt from scratch, reducing the risk of configuration drift and unauthorized changes.
Incident Management:
Automated Incident Response:
Set up automated incident response mechanisms to detect and respond to security incidents in real-time, such as deploying fixes or rolling back changes automatically.
Post-Incident Analysis:
Conduct thorough post-incident analyses to understand the root cause of security incidents and implement necessary improvements to prevent their recurrence.
Secrets Management:
Secrets Vault:
Utilize a centralized secrets management system like HashiCorp Vault or AWS Secrets Manager to securely store and manage sensitive information such as API keys, passwords, and certificates.
Dynamic Secrets:
Implement dynamic secrets where possible, generating short-lived credentials dynamically to minimize exposure in case of a breach.
Vulnerability Scanning:
Continuous Monitoring:
Integrate automated vulnerability scanning tools such as Nessus, OpenVAS, or Qualys into your CI/CD pipeline to continuously monitor for known vulnerabilities in dependencies and infrastructure components.
Dependency Management:
Regularly update and patch dependencies to mitigate known vulnerabilities, and automate vulnerability checks for third-party libraries.
Access Control:
Role-Based Access Control (RBAC):
Implement RBAC to enforce the principle of least privilege, ensuring that users and components only have access to the resources and actions necessary for their role.
Multi-factor authentication (MFA):
Require MFA for accessing critical components of the CI/CD pipeline, such as the version control system or FF, to add an extra layer of security.
By addressing these core aspects of CI/CD security and implementing best practices at each stage of the pipeline, organizations can enhance the security posture of their software delivery processes and minimize the risk of security breaches.
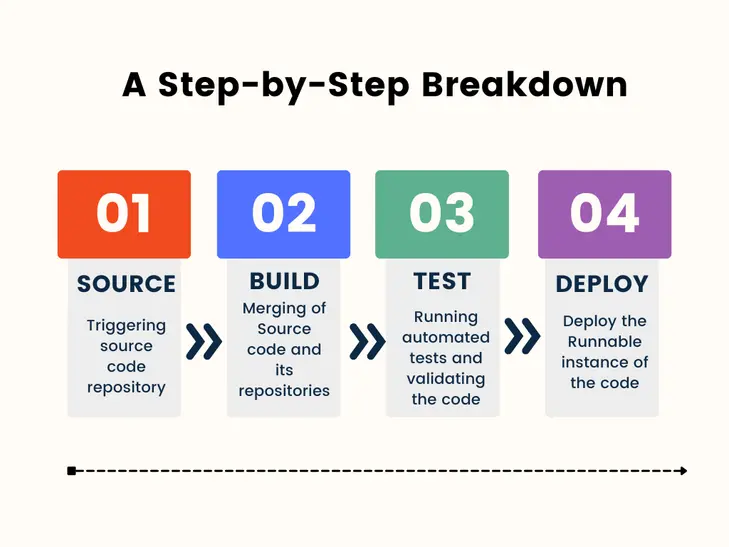
Streamlining Development: A Step-by-Step Breakdown
These are the typical stages of a CI/CD pipeline, which are mentioned below:
Source Phase
This is where developers make changes to the codebase. The source phase involves version control systems such as Git, where developers commit their code changes. CI tools like Jenkins, GitLab CI, or Travis CI monitor these repositories for changes.
Build Phase
In the build phase, the code is compiled, packaged, and prepared for deployment. This phase includes tasks such as compiling source code, resolving dependencies, and generating artifacts. Build automation tools like Maven, Gradle, or Docker are often used in this phase to streamline the process.
Test Phase
Testing is a crucial part of the CI/CD pipeline. In this phase, various types of tests are performed to ensure that the code changes meet quality standards and don't introduce regressions. These tests may include unit tests, integration tests, functional tests, and acceptance tests. Automated testing frameworks such as JUnit, Selenium, or pytest are commonly used in this phase.
Deploy Phase
The deploy phase involves deploying the built and tested code to the target environment. This could be a development, staging, or production environment, depending on the deployment strategy. Automation tools like Ansible, Puppet, or Kubernetes are often used to deploy applications consistently and reliably across different environments.
Each of these stages plays a critical role in the CI/CD process, helping to automate and streamline the software delivery pipeline from code changes to deployment.
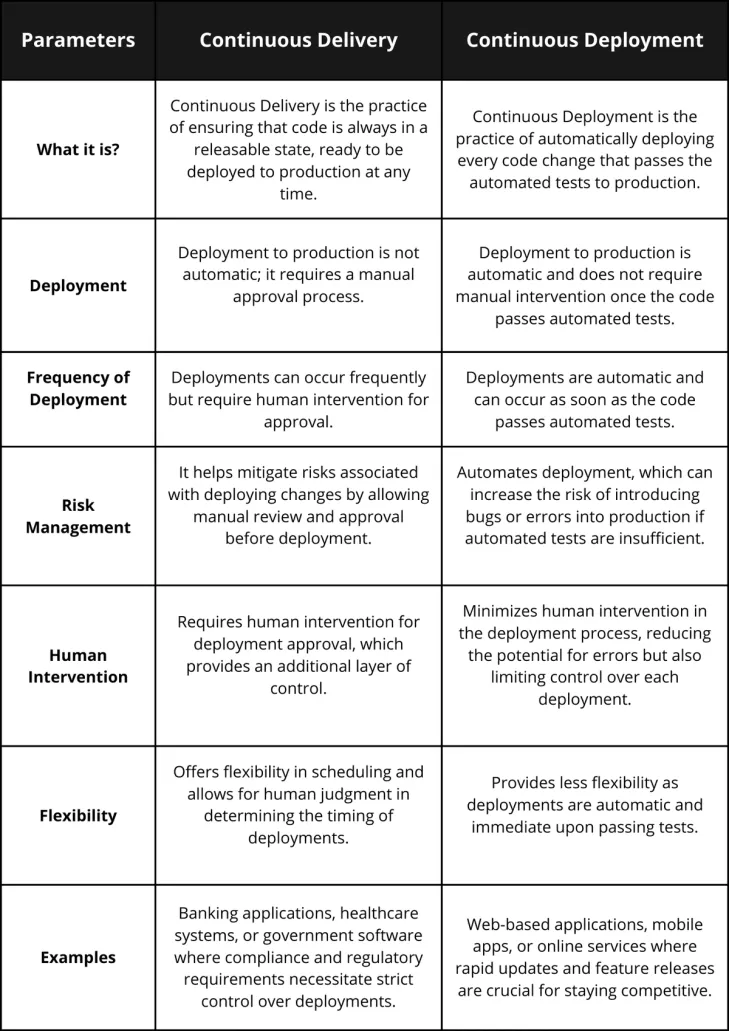
Key Differences between Continuous Delivery and Continuous Deployment
Here are the key differences between continuous delivery and continuous deployment, presented in a tabular format for easy comparison:
Security Risks in CI/CD Pipelines
This section identifies and discusses the most common security risks and challenges associated with CI/CD pipelines, such as unauthorized access, code injection, and data breaches:
Vulnerabilities in Third-Party Dependencies
CI/CD pipelines often rely on various third-party dependencies, such as libraries and frameworks, to streamline development and deployment processes. However, these dependencies can introduce security risks if they contain vulnerabilities. Attackers can exploit known vulnerabilities in third-party dependencies to gain unauthorized access, execute arbitrary code, or compromise the integrity of the pipeline.
Insider Threats and Malicious Code Injection
Insider threats refer to security risks posed by individuals within an organization who have access to the CI/CD pipeline. Malicious actors may inject unauthorized or malicious code into the pipeline to compromise its functionality or steal sensitive data. Malicious code injection can lead to the deployment of compromised or vulnerable applications, unauthorized data access, or sabotage of the pipeline infrastructure.
Data Exposure and Leakage During Pipeline Execution
CI/CD pipelines often involve the processing and manipulation of sensitive data, such as credentials, configuration files, and customer information. Data exposure and leakage can occur during pipeline execution due to misconfigurations, insecure storage practices, or inadequate data handling procedures. Unauthorized access to sensitive data during pipeline execution can result in data breaches, regulatory non-compliance, reputational damage, and financial losses.
Ensuring CI CD Security with Top 5 Best Practices
Ensuring CI/CD security is crucial for maintaining the integrity and reliability of software development pipelines. Here are the top 5 best practices to enhance it:
Implement Secure Pipeline Configuration:
Ensure that your CI/CD pipeline configurations are stored securely and access is restricted to authorized personnel only. Use secrets management tools to securely store sensitive information such as API keys, passwords, and tokens, and never hardcode them directly into pipeline scripts or configuration files. Regularly review and audit pipeline configurations for any security vulnerabilities or misconfigurations.
Integrate Automated Security Testing:
Incorporate automated security testing into your CI/CD pipeline to scan code for vulnerabilities, such as static application security testing (SAST), dynamic application security testing (DAST), and dependency scanning. Use tools like SonarQube, OWASP ZAP, or Snyk to automatically detect and mitigate security issues early in the development lifecycle. Ensure that security tests are run as part of the pipeline's automated testing suite and that failing tests trigger alerts for immediate remediation.
Enforce the Least Privilege Principle:
Follow the principle of least privilege by granting only the minimum level of access required for each user, service account, or CI/CD agent. Use role-based access control (RBAC) mechanisms to enforce granular permissions and restrict access to sensitive resources within the CI/CD environment. Regularly review and update access controls to align with the principle of least privilege and remove unnecessary permissions.
Continuous Monitoring and Logging:
Implement robust logging and monitoring mechanisms within the CI/CD pipeline to track and analyze activities, detect anomalies, and identify security incidents in real-time. Integrate security information and event management (SIEM) systems or log aggregation platforms to centralize logs from various pipeline components and facilitate proactive threat detection and incident response. Regularly review and analyze pipeline logs for suspicious activities, unauthorized access attempts, or other security-related events.
Secure Infrastructure as Code (IaC):
Treat Infrastructure as Code (IaC) with the same level of security scrutiny as application code.
Use infrastructure provisioning tools like Terraform, Ansible, or AWS CloudFormation securely by implementing secure coding practices, such as parameterization, version control, and automated testing. Regularly scan IaC templates and configurations for security vulnerabilities using tools like Checkov or Terraform's built-in validation features, and remediate any issues promptly.
Leveraging CI/CD Security Tools for a Fortified Pipeline
Ensuring the security of these pipelines is essential to protecting the integrity of software releases and preventing potential breaches. Here are some security tools commonly used in CI/CD pipeline environments:
SonarQube
SonarQube is a widely used static code analysis tool that identifies code quality issues, security vulnerabilities, and bugs. It integrates with CI/CD pipelines to provide continuous inspection of code as it is built. By integrating security-focused static analysis into the CI/CD pipeline, SonarQube helps identify and remediate security weaknesses early in the development process, reducing the risk of security breaches and vulnerabilities making their way into production. SonarQube provides a free trial, with pricing starting at $160 per year.
Checkmarx
Checkmarx is a provider of software security solutions specializing in static application security testing (SAST), software composition analysis (SCA), and other related services. It helps identify security vulnerabilities, including those in open source components, and integrates with CI/CD pipelines for automated security testing. It also supports 50+ languages and 100+ frameworks for a wide range of software projects.
Aqua Security
Aqua Security provides container security solutions that integrate with CI/CD pipelines. It offers vulnerability scanning, runtime protection, and compliance automation for containerized environments. It supports deployment across various cloud platforms, including AWS, Azure, Google Cloud Platform (GCP), and Kubernetes-based on-premises environments. It ensures consistent security policies and enforcement across hybrid and multi-cloud environments.
Exploring the Untapped Potential of CI/CD Security
This section explores the advantages and positive outcomes of implementing robust security measures within CI/CD pipelines to protect software development processes and assets:
Early Detection of Vulnerabilities:
CI/CD security allows for continuous testing and scanning of code throughout the development process, enabling the early detection of security vulnerabilities.
Rapid Response to Threats:
With automated security checks integrated into the CI/CD pipeline, teams can respond quickly to security threats, reducing the time it takes to address and mitigate risks.
Improved Code Quality:
By incorporating security checks into the automated build and deployment process, CI/CD encourages developers to write more secure code, leading to overall better code quality.
Consistency in Security Measures:
CI/CD security ensures that security practices are consistently applied across all stages of the development pipeline, reducing the risk of oversight or human error.
Cost Savings:
Identifying and fixing security vulnerabilities early in the development lifecycle is generally less expensive than addressing them later in production. CI/CD security helps mitigate potential financial losses due to security breaches.
Emerging Trends of CI/CD security in 2024
As we progress through the year, keep an eye out for these notable CI/CD security trends in 2024:
Increased usage of DevSecOps
According to Palo Alto's Unit 42 report, the cloud is the primary target for cyber attacks, with 80% of security exposures occurring in cloud environments, compared to only 19% in on-premise setups. The report highlights the dynamic nature of cloud infrastructure, where changes of over 20% occur monthly across industries, leading to nearly half of high-risk exposures resulting from constant cloud service updates.
To tackle these risks, DevSecOps integrates security measures directly into the DevOps workflow, rather than treating security as a separate concern addressed at the end of development. This demonstrates that DevSecOps guarantees that security remains a central focus throughout the entire software development lifecycle.
Applying Machine Learning for Threat Detection
Machine Learning and Artificial Intelligence will play a larger role in threat detection and security analytics. CI/CD pipelines may leverage machine learning algorithms to analyze vast amounts of data and identify potential security threats in real-time. For example, if an ML model identifies a suspicious network connection or unusual system activity, it can trigger automated actions such as isolating the affected system, blocking malicious IP addresses, or alerting security personnel for further investigation.
Integration of Infrastructure as Code (IaC) Security
Market and Markets reported that the worldwide market size for infrastructure as code reached USD 0.8 billion in 2022 and is anticipated to achieve USD 2.3 billion by 2027, with a projected compound annual growth rate (CAGR) of 24.0% during the forecast period. As IaC becomes standard, the need for securing infrastructure definitions and configurations in the CI/CD process intensifies. Approximately 40% of organizations might adopt IaC security scanning tools within their pipelines by 2024 to detect misconfigurations and compliance violations early.
Wrapping Up
As CI/CD practices become increasingly prevalent in software development, ensuring the security of the pipeline becomes important. The future of CI/CD security will likely expand to incorporate more advanced threat detection mechanisms, enhanced automation, and tighter integration with DevSecOps practices.
At SoluteLabs, we understand the critical importance of CI/CD security in today's software development landscape. Our comprehensive suite of services is designed to address the security challenges inherent in CI/CD pipelines. Get in touch with us to transform your vision into reality within the designated timeline.
Frequently Asked Questions
Have a product idea?
Talk to our experts to see how you can turn it
into an engaging, sustainable digital product.